What are DDoS Attacks?
Websites are essential to businesses. They serve as our brand ambassadors, communication centers, and stores. However, we are also constantly exposed to a plethora of security risks because of our digital footprint, and DDoS attacks are at the top of the list.
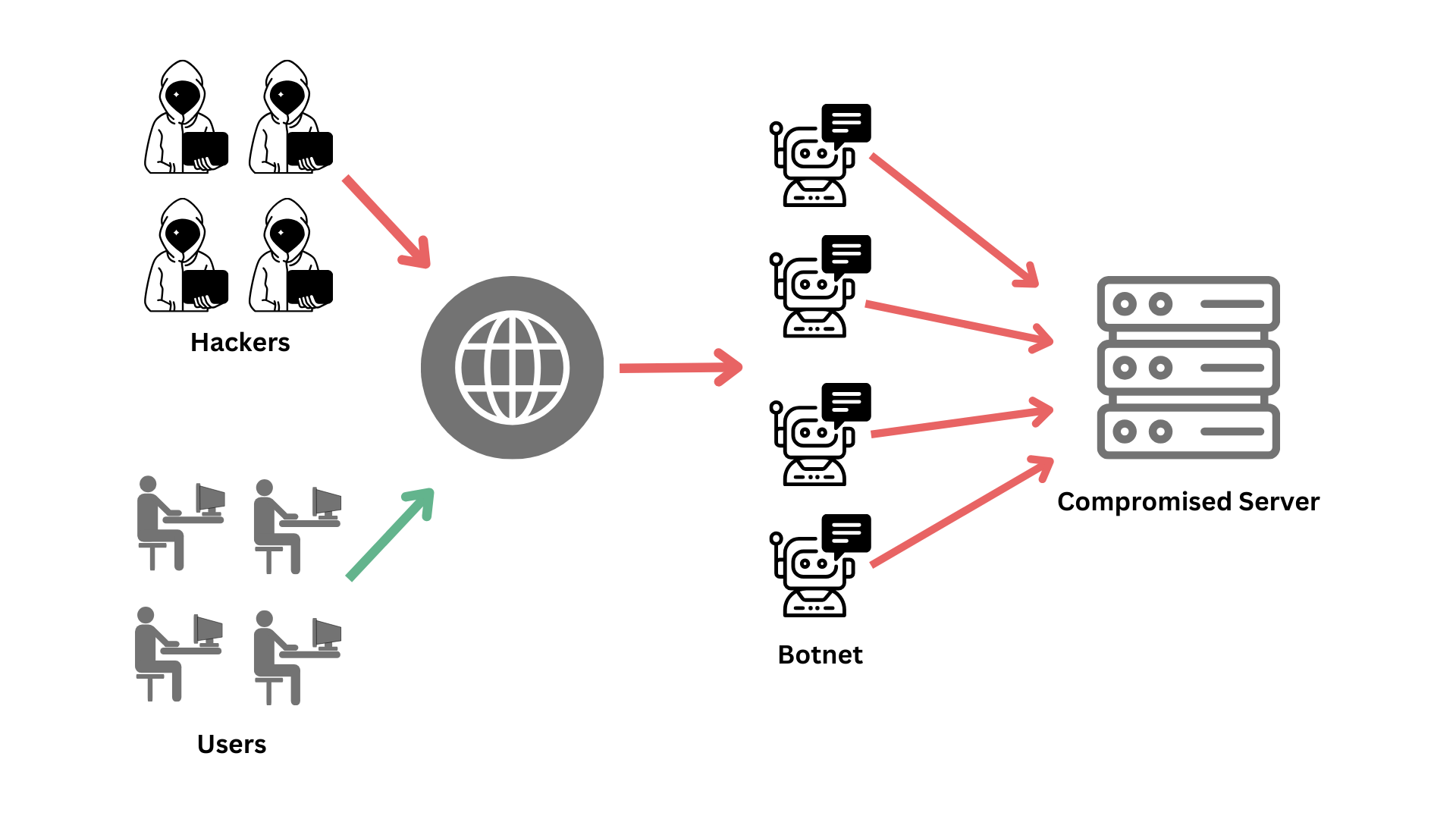
An attack known as a DDoS (Distributed Denial-of-Service) attempts to stop legitimate users from accessing a website or server by flooding it with fraudulent traffic. A DDoS assault is essentially like trying to pass through a door on a packed street with too many people.
These assaults have the potential to be quite disruptive, leading to monetary losses, harm to one’s reputation, and irate clients. So, how do hackers carry out denial-of-service attacks, and how can you recognize and defend against these risks?
How to DDoS: A Step-By-Step Guide to Stress Testing
Step 1: Understand the Legality and Ethics
Before considering a DDoS attack, ensure you understand the legal and ethical implications:
- Legal Issues: Unauthorized attacks are illegal.
- Ethical Hacking: Use DDoS attacks only for stress testing with explicit consent and legal agreements in place.
- Consent and Control: Ensure you have the organization’s explicit consent and can control the attack to avoid real harm.
Step 2: Choose Your Method
There are several methods for stress testing, varying in complexity and impact.
- Using Botnets:
- Definition: A botnet is a collection of compromised devices controlled by a Command-and-Control (C&C) center.
- Usage: Botnets can launch large-scale DDoS attacks by sending large amounts traffic to the target.
- Availability: Some botnets are available for rent, often used for illegal activities such as spam, phishing, or cryptocurrency mining.
- Using DDoS Programs and Tools:
- Individual Efforts: Small-scale hackers without botnet access use specialized tools to direct traffic from their computers.
- Crowdsourcing: Gathers multiple users to download and use tools simultaneously, increasing the attack’s impact.
- Tools List:
- HULK (HTTP Unbearable Load King)
- XOIC
- R-U-Dead-Yet
- Low Orbit Ion Cannon (LOIC)
- Tor’s Hammer
- DDOSIM – Layer 7 DDoS Simulator
Step 3: Establishing a Botnet
If using a botnet, the following steps are typically involved:
- Infect Devices: Spread malware to compromise a network of devices, creating a botnet. This includes computers and IoT devices.
- Control the Botnet: Use a Command-and-Control center to manage the infected devices.
- Send Commands: Direct the botnet to send requests to the target’s IP address, overwhelming the server or network.
Step 4: Launching the Attack
Whether using a botnet or DDoS tools, follow these steps to launch the attack:
- Preparation: Ensure all tools, devices, and personnel are ready.
- Coordination: If crowdsourcing, coordinate with participants to launch the attack simultaneously.
- Execution: Direct the traffic to the target’s IP address.
- Monitoring: Carefully monitor the attack to control its impact and avoid causing unintended damage.
How Can I Spot a DDoS Attack?
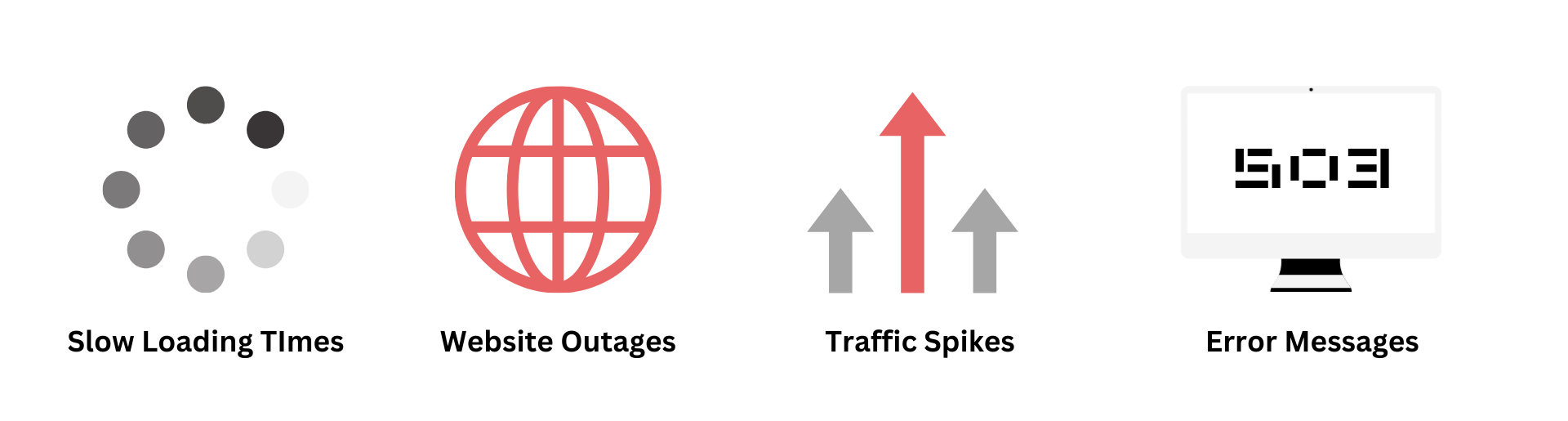
DDoS attacks can manifest in various ways, but some common signs include:
| Sign | Description |
Slow website loading times |
This indicates that your server is struggling to handle an unusually high volume of traffic. |
Complete website outages |
If your website becomes entirely inaccessible, a DDoS attack could be the culprit. |
Unusual traffic patterns |
Spikes in Google Analytics traffic from unexpected locations or a single source can be red flags. |
Error messages |
Server overload errors often accompany DDoS attacks. |
Pro tip: If you experience any combination of these signs, staying calm and alerting your engineering team to take immediate action is crucial.
How Can I Build a Stronger Defense to Mitigate Attacks?
There are strategies to combat DDoS attacks. Here are some key steps to consider:
| Strategy | Description |
Utilize a DDoS mitigation service |
Partnering with a reliable security provider like HorizonIQ provides a defense system that filters out malicious traffic before it reaches your servers, keeping your website operational. |
Implement rate limiting |
Restricts the number of requests a single IP address can send to your server within a specific timeframe, preventing a flood of traffic from a single source. |
Regularly update software |
Keeping software up-to-date with the latest patches reduces vulnerabilities that attackers may exploit. |
Educate employees on DDoS attacks |
Training employees on cyber security best practices can help them recognize phishing attempts and reduce the risk of DDoS attacks. |
Why Should I Choose HorizonIQ for DDoS Mitigation?
At HorizonIQ, we know how vital your website is to the success of your company. That is why we provide a full range of DDoS protection services at our Secaucus, Amsterdam, Chicago, and Phoenix data centers to safeguard your online presence.
What distinguishes us?
- Advanced threat detection: We can minimize disruptions by using our state-of-the-art technology to quickly identify and filter out unwanted communications.
- Global network infrastructure: We can efficiently absorb and mitigate DDoS attacks from any location in the world thanks to our carefully positioned data centers.
- Expertise in security available around the clock: We have seasoned security specialists on hand to keep an eye on your network and proactively counter attacks.
Don’t let a DDoS attack cripple your business. By understanding DDoS attacks, implementing mitigation strategies, and partnering with a trusted provider like HorizonIQ, you can build a robust defense protected from fast-moving, high-volume, encrypted, or very short-duration threats.
Contact us today and explore our best-in-class DDoS protection solutions.
Please note: While HorizonIQ offers a variety of security solutions globally, DDoS mitigation is currently available at our data centers in Amsterdam, Chicago, Phoenix, and Secaucus.