Month: July 2020

Cyber Threats Don’t Shut Down for COVID-19
Today we are pleased to welcome guest blogger Tony Bradley, Senior Manager of Content Marketing for Alert Logic, INAP’s trusted managed security partner and expert in cloud security for financial services customers.
– Wendy Williams, Product Manager, INAP
Thanks to the COVID-19 pandemic, we are living in a different world now than the one we had at the beginning of 2020. Everything has changed in terms of how businesses communicate and operate, but some things haven’t changed. In spite of the dramatic shift in the world in general, it is still business as usual for cyber attacks and cybersecurity.
Everything Has Changed for Companies
Companies of all sizes and across all industries have been forced to find ways to remain productive and keep the business going while suddenly working with an entirely remote workforce.
What does that mean from a cybersecurity perspective? It means that users who were previously sitting in an office using company-issued computers connected to a company-managed network are now getting their work done on a random collection of personal and business devices connected to the public internet over their home Wi-Fi networks. The complexity of the environment has skyrocketed, and the exposed attack surface has expanded exponentially.
Cyber Attacks Are on the Rise
As challenging as things have been this year for businesses and individuals, the reality is that cyber attackers don’t care about the COVID-19 pandemic, or whether you’re quarantined or not. On the contrary, the chaos and confusion of the sudden shift to working remote and the expansion of the attack surface represent a major opportunity for attackers to exploit.
Most users are more exposed on their home networks and lack the filters and security controls that exist on a corporate network. The unprecedented situation we are facing has changed standard processes and methods of communication, making it more difficult to determine what is legitimate and what seems suspicious. Employees are also anxious for information and more likely to click on links or open attachments they shouldn’t. As a result, attackers have ramped up phishing, ransomware and business email compromising attacks.
The Need for Visibility and Vigilance
It is more important than ever for organizations to have visibility of all endpoints and all activity. That means increasing visibility to encompass the dramatically expanded attack surface, including personal endpoints connected to remote networks. Increased focus on suspicious activity on cloud platforms and cloud-based SaaS (software-as-a-service) applications is also necessary.
It’s also critical to understand that attackers don’t have business hours. Not only is it always the middle of the day somewhere on the planet, but many attacks—at least the initial exploit that gets attackers through the door—are automated and run around the clock. Organizations need to be vigilant, and that means having security experts monitoring endpoints and activity 24/7 to identify and respond to suspicious or malicious activity.
Value of MDR
Businesses have enough to worry about, and very few have the tools or people necessary for effective cybersecurity. This is especially true given the COVID-19 pandemic and expanded attack surface of users connecting from personal devices and home networks. The best strategy is to stay focused on the core strengths of the company and satisfying customers, while engaging with a trusted partner to provide the cybersecurity visibility and vigilance you need.
Working with a managed detection and response (MDR) provider enables an organization to get the protection and peace of mind they need. INAP and Alert Logic have a strong partnership and provide deep, focused cybersecurity expertise to keep your networks and data safe and give you confidence in your cybersecurity even during these unprecedented times.

About the Author
Tony Bradley is Senior Manager of Content Marketing for Alert Logic. Tony worked in the trenches as a network administrator and security consultant before shifting to the marketing and writing side of things. He is an 11-time Microsoft MVP in security and cloud and has been a CISSP-ISSAP since 2002. Tony has authored or co-authored a dozen books on IT and IT security topics, and is a prolific contributor to online media sites such as Forbes and DevOps.com.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

COVID-19 Pandemic Shines Spotlight on How Essential Soft Skills are to the Future of Tech
In the day-to-day life of a workplace, success often hinges on how well a team works together. All the technical skill in the world won’t help an IT team or company reach its goals if it’s plagued by poor communication, poor leadership and lack of flexibility, among other things. These soft skills have proven even more important in the age of COVID-19, with a rise in remote work and the corresponding shift in the ways we work with each other.
Even before COVID-19 disrupted work as we know it, soft skills were so important that one study found 67 percent of human resources professionals declined to offer a job to an otherwise qualified technology candidate because of a lack of soft skills.
Prior to the pandemic, we asked 500 senior IT professionals and infrastructure managers to rank the soft skills they thought would be most important for future IT professionals to possess. The attributes were ranked 1-6, with 6 being the least important. Below are the average ranks.
Most Important Soft Skills for Future IT Professionals
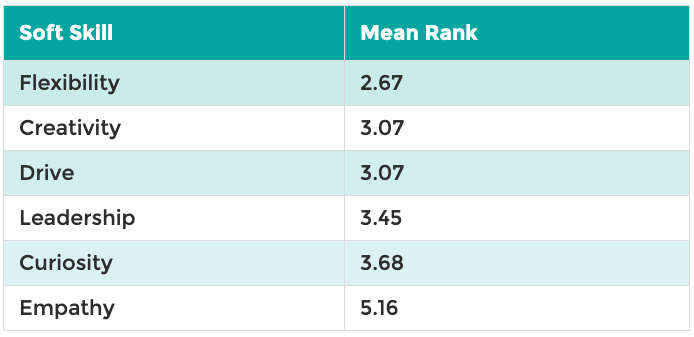
Since these results were collected, the world has obviously changed. And yet, our “new normal” only underscores the results.
Flexibility Is the No. 1 Soft Skill for IT Pros
Based on the rapid changes we’ve seen in tech and the world at large, it should come as no surprise that “flexibility” was ranked most important. Working with a team that’s willing to step up to the plate and roll with the punches will lead to better outcomes than working with players who are rigid and unwilling to bend as priorities shift.
“Hiring managers need to identify flexibility as a key behavior and skill set during the hiring process,” said Jackie Coats, INAP’s Senior Vice President of Human Resources. “To evaluate it, have the candidate explain a time when they had to deal with an unforeseen situation, and what they did to accomplish their goal regardless of the surprise.”
Business priorities are often adjusted and the demand on IT teams will move with them. Or a team member might leave unexpectedly, and the rest of the team will need to fill in.
“Another question to determine flexibility would be to ask how the employee has helped outside of their role when the team was short-staffed or under a tight deadline,” Coats added.
As we’ve seen remote work become the norm for many businesses, flexibility is an important trait for both employees and for supervisors to possess.
“Being flexible during these times is a critical tool we as leaders must leverage,” said Matt Cuneio, INAP’s Vice President, Global Support. “Nothing is more important to the health of a team than confidence that we’re all in this together. We’re going to be flexible with each other, ensuring we all win.”
A Need for Innovation Necessitates Creativity
Change often feels unexpected, as we’ve seen with the pandemic, but it’s always inevitable. In another pre-pandemic survey, we wanted to get an idea of what exactly will be driving change in IT roles now and in the future, so we asked our participants to choose the top driver. The need for innovation took the top spot, selected by 27 percent of participants. (Robust security and infrastructure scalability came in a close second and third.)
All of this change and need for innovation emphasizes the importance of creativity — the second ranked soft skill for IT pros. IT teams are also asked to problem solve on a daily basis and come up with new solutions to help the business achieve its goals or to find solutions to unique problems, like how to adjust networking strategies for a decentralized workforce.
Undervalued Empathy?
Empathy is the ability to identify with another person by sharing in their perspective and feelings. This soft skill is commonly valued in the helping professions, like counseling and social work, but can bring great value to teams in all professions by helping develop camaraderie and trust. Yet empathy ranked lowest on our list.
Cuneio shared his thoughts on the impact of empathy for IT, both within a team setting and with customers. “I had a friend tell me once, ‘Listen to understand.’ A listening ear is a powerful and necessary tool in today’s world,” he said.
Fostering empathy between individuals helps people feel heard and understood, which in teams can benefit collaboration and brainstorming sessions where colleagues feel empowered to share ideas.
“Every interaction you have is an opportunity to impact someone’s life,” Cuneio added. “It always amazes me the response I get by asking the simple question ‘How are things?’ The key component to this question is to listen and inquire to the response.”
It’s also been shown that companies that have a more empathetic culture outperform less empathetic companies by 20 percent. The bottom line: Individual empathy shouldn’t be overlooked.
Explore HorizonIQ
Bare Metal
LEARN MORE
Stay Connected

Dedicated Private Cloud vs. Virtual Private Cloud: What’s the Difference?
What is the difference between a dedicated private cloud and a virtual private cloud? As solutions architects, this is a question my teammates and I hear often. Simply put:
- Dedicated Private Cloud (DPC) is defined as a physically isolated, single-tenant collection of compute, network, and sometimes storage resources exclusively provisioned to just one organization or application.
- Virtual Private Cloud (VPC) is defined as a multi-tenant but virtually isolated, collection of compute, network, and storage resources.
A simple analogy comparing the two would be choosing between a single-family private home (DPC) versus a condo building (VPC).
Despite the differences, both dedicated and virtual private clouds offer secure environments with flexible management options, which allow you to concentrate on your core business instead of struggling to keep up with daily infrastructure monitoring and maintenance.
Let’s discuss each cloud product in greater depth and review use cases for dedicated vs. virtual private clouds. I’ll use HorizonIQ’s dedicated private cloud (DPC) and virtual private cloud (VPC) products as examples for the DPC and VPC differentiators.

What is a Dedicated Private Cloud (DPC)?
DPCs are scalable, isolated computing environments that are tailored to fit unique requirements and rightsized for any workload or application. DPCs are ideal for mission-critical or legacy applications. When applications can’t be easily refactored for the cloud, a DPC can be a viable solution. DPC is also ideal for organizations seeking to reduce time spent maintaining infrastructure. You do not need to sacrifice control, compliance, or performance with a DPC. HorizonIQ DPCs are built with trusted enterprise-class technologies powered by VMware or Hyper-V.
DPC use cases:
- Compliance and audit requirements, such as PCI or HIPAA
- Stringent security requirements
- Large scale applications with rigorous performance and/or data storage requirements
- Legacy applications, which may require hardware keys or specific software licensing components
- Data center migration — scale physical compute, network, and storage capacity as needed without significant investments in data center build outs
- Complex network requirements, which may include MPLS, SDWAN, private layer 2 connections to customers, vendors or partners
- Fully integrated active or hot-standby disaster recovery environments
- Infrastructure Management Services, all the way to the operating system
- High CPU/GPU/RAM requirements
- AI environments
- Big Data
- Always on applications that are not fit for hyper-scale providers
HorizonIQ’s DPC differentiators:
- Designed and “right-sized” to fit your application, economics and compliance requirements
- Built with enterprise-class technologies and powered by VMware or Hyper-V.
- Utilize 100 percent isolated compute and highly secure, single-tenant environments perfect for PCI or HIPAA compliance.
- Flexible compute and data storage options that allow you to meet any application performance and growth requirements.
- OS Managed services free up time from routine tasks of patching
- Transparency into the core infrastructure technology allows you complete visibility in the inter-workings of the environment.
- No restrictions on sizing of the VMs or application workloads because the infrastructure is custom designed for your organization’s specific technology needs.
- SDN switching for flexible, quick, and easy network management or dedicated switching for complex network configurations to meet any network requirements.
- MDR security services available, which include vulnerability scanning, IDS/IPS, log management with SOC (Security Operations Center)
- Off-site cloud backups and fully integrated and managed DRaaS available.
What is a Virtual Private Cloud (VPC)?
VPCs are ideal for applications with variable resource requirements and organizations seeking to reduce time spent maintaining infrastructure without sacrificing control of your virtual machines, compliance, and elasticity. They provide a customized landscape of users, groups, computing resources and a virtual network that you define. Different organizations or users of VPC resources do not have access to the underlying hypervisor for customization or monitoring plugin installation.
VPCs are pre-designed for smaller to medium workloads and provide management and monitoring tools. They allow for fast application deployment because the highly available compute, security, storage, and hypervisors are already deployed and ready for your workload.
VPC use cases:
- Small to medium-sized workloads with 10 to 25 VMs and simple network requirements
- Applications with lower RAM requirements
- Ideal for additional capacity needed for projects. Deploy in hours—not days.
- Quickly spin up unlimited Virtual Machines (VMs) per host to support new projects or peak business cycle’s ability to quickly add resources on demand
HorizonIQ’s VPC differentiators:
- Designed for fast deployments enabling you to eliminate lengthy sourcing and procurement timelines
- Shield Managed Security services included
- 24/7 physical security in SSAE 16/SOC 2 certified Data Centers
- Private networks & segmentation
- Account security for secure portal access
- DDoS protection & Mitigation
- OS Managed services free up time from routine tasks of patching
- Easy to use interface simplifies management and reduces operational expense of training IT staff
- Off-site Cloud Backups and Fully integrated On-Demand (Paygo) DRaaS available
- MDR security services available, which include vulnerability scanning, IDS/IPS, log management with SOC (Security Operations Center)
DPC vs VPC: Which is Right?
Do you know which private cloud model will work with your company’s workload and applications? Whether you’re certain that a DPC or VPC will be a good fit or you’re still unsure, HorizonIQ’s experts can help take your cloud infrastructure to the next level. Chat today to talk all things private cloud.









